Greetings, dear readers!
The problem of security has recently become very urgent due to the enormous number of hacks and security incidents in the Web3 sphere. Everyone has very different ideas and suggestions on this topic, so we will only attempt to describe a portion of them today.
To let us know your interests and preferences better, please fill in a short questionnaire!
https://docs.google.com/forms/d/e/1FAIpQLSckhaBICyiJLanepidb6MEcuoMX7826bmMDcJaIm21Yf0LEuQ/viewform
So, what are the chances of enhancing current techniques with additional security, and how precisely is the security of the protocol formed in terms of audit and logic?
Important disclaimer — I am an employee of the auditing company Pessimistic and a former employee of Immunefi. This article presents my subjective perception of the market — this is not a market research, but an overview. I also don’t want to criticize any of the platforms presented in the article — on the contrary, I understand the business decisions behind their actions and I believe they have the right to exist in any case!
First, we will attempt to comprehend what a bug bounty is, why it is necessary, and why it cannot replace auditing but can work in concert with it to, for example, make a protocol safer.
It will be fascinating as we weigh the main drawbacks and benefits of current solutions from the perspectives of the project, the auditor, and bug bounty hunters!
Let’s get is started! Join the Discord server below & stay tuned!
Bug Bounty Meets Web3
Web3 bug bounty platforms and CTFs play a significant role in identifying and mitigating security vulnerabilities in the blockchain industry. On October 10 1995, Netscape launched the first technology bug bounty program for the Netscape Navigator 2.0 Beta browser.
This was only the beginning of the huge sphere of bug bounty that we have now!
Nowadays, companies can navigate the cybersecurity landscape with resilience and peace of mind by strategically employing bug bounties and establishing strong foundations through effective quality control, relationship building, and scaling. The programs are adaptable and can quickly scale as needs arise.
This could result in the discovery of known and unknown security flaws in any organization. With this many targets, it is impossible for a single security team to test them all. As a result, they choose to externalize the issues by launching bounty campaigns on platforms with large communities of experts.
Each of the platforms below provides unique features and solutions to enhance web security, giving users a range of tools to safeguard their digital assets. Let’s check them out!
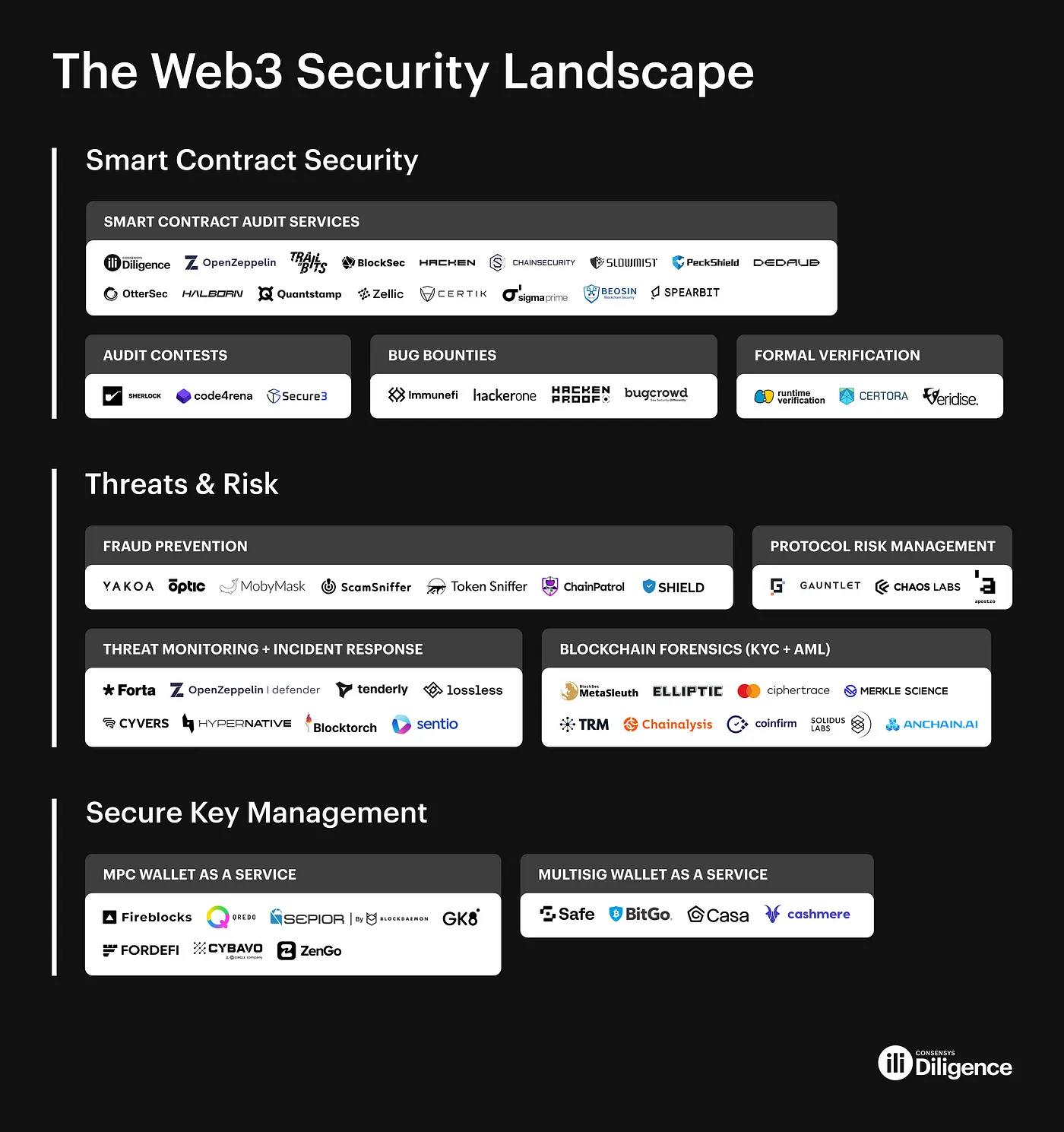
Here are some popular Web3 bug bounty platforms:
-
1. Code4rena
-
2. Sherlock.xyz
-
3. Immunefi
-
4. Hackerone
-
5. BugCrowd
-
6. Hackenproof
-
8. Bugrap
-
9. Hats.Finance
-
10. Spearbit
-
11. Yaudit
-
12. Auditjobs
And a few platforms that have not yet begun to position themselves as such, but their services are sometimes used by Web3 projects:
-
Intigriti — one of Europe’s leading crowdsourced cybersecurity firms that have bug bounty programs;
-
Synack — the company uses a crowdsourced network of white-hat hackers to find exploitable vulnerabilities and a SaaS platform enabled by AI and machine learning to identify exploitable vulnerabilities;
-
Open Bug Bounty — open, disintermediated, cost-free, and community-driven platform.
All of the projects’ approaches differ drastically right away, and they can be roughly divided into two categories: classic and novel. The first is primarily made up of players who are already well-known to us in the bug-bounty Web2 market.
https://github.com/sw33tLie/bbscope
We can say that out of all of them, Immunefi stands out. In my opinion, Immunefi is a logical continuation of H1 and other similar Web3 sites.
Recently, they have come in for a lot of criticism, but to me, it makes perfect sense because the project itself determines the scope of the reported vulnerability; and such platforms are frequently created in Web2 for state corporations and big businesses.
The Pentagon’s use of bug bounty programs is part of a posture shift that has seen several US Government Agencies reverse course from threatening white hat hackers with legal recourse to inviting them to participate as part of a comprehensive vulnerability disclosure framework or policy.
It is also impossible to say that they are against bug bounty hunters because the revenue of these sites comes from paying for vulnerabilities discovered, so it is in the project’s best interest to do so. It’s crucial to keep in mind that the financial model of such platforms is first and foremost that they only receive payment after a bug bounty hunter has successfully found a vulnerability.
Let’s also keep in mind that this is a crucial point: typically, a project does not need to deposit funds or make a payment in order to place its bug bounty program initially.
https://github.com/pessimistic-io/slitherin#acknowledgements
However, a lot of platforms, including Immunefi, started to request deposits due to the large number of fraudulent (scam) projects. One way or another, Immunefi started and worked for a long time following the first model, so we are going to look at it further — in a raw form, without complications.
Classic or Novel ?
We now arrive at the main issue: what is a bug bounty and what is it actually used for?
The problem is that, in how the project sees it, the scenario is frequently something along the lines of “let’s imagine that some evil hacker from a dark forum will suddenly decide to hack us, google information about us, will see that we have a bug bounty and will send vulnerability there to get legal money.”
There is therefore some truth to it, but regrettably it doesn’t always work that way and frequently doesn’t aid in preventing hacking. So what should one do to assist a company that requires protection?
Let’s start with some common sense: the bug bounty platform itself has a business interest in our formula…
https://mirror.xyz/c4blog.eth/F5AlESDsm304ziAVWGn07WfmTy-TFwvBNA1NdDI-s2o
It’s also crucial to demonstrate to the company that it works hard and is helpful, but how exactly?
The solution is pretty straightforward: build your own community of experts, like in those aforementioned dark forums, so they can identify all vulnerabilities faster because the bug bounty program will draw their attention.
Unlike pentests, smart contract audits differ in a few meaningful ways: smart contract audits are performed on open-source applications that are small enough to be manually reviewed in their entirety. They culminate in a report intended to be for both the development team and the community at large.
The following are some well-liked “classic” Web3 bug bounty programs:
-
Immunefi — Immunefi is a bug bounty platform that offers DeFi protocol security services. Immunefi is intended to provide high-level blockchain security while also ensuring that rewards are distributed consistently and transparently. Immunefi includes a bug reporting system, bounty rewards, and a security evaluation. It also allows for the detection of vulnerabilities in smart contracts, chains, and web channels for various blockchain infrastructures.
-
Hackerone — Hackerone is a platform that provides a comprehensive suite of web application and website security testing and vulnerability discovery services. The platform is well-known for its crowdsourced approach to security testing, which allows independent researchers to report security flaws on organizations’ behalf. Hackerone is based on a tried-and-true strategy that combines crowd-sourced expertise with cutting-edge technology to provide clients with a scalable, cost-effective way to secure their applications.
-
BugCrowd — BugCrowd is a feature-rich bug bounty platform that delivers quick and accurate assessments by combining human expertise, technology, and a large community of security researchers. BugCrowd’s security solutions aid in the identification, prioritization, and management of potential vulnerabilities in web applications. The platform integrates with various development environments and enables developers and security researchers to collaborate seamlessly.
So we move on to the more modernistic (novel) platforms, and the main difference is that they support both the bug-hunter, the Project and the community. Frequently, a project must secure a payout and deposit in advance so that the triager can make an unbiased decision.
The following are some examples of Web3 bug bounty platforms, along with detailed descriptions:
-
Code4rena — Code4rena is a platform that offers competitive programming, auditing, and bug bounty services for smart contract development. Code4rena hosts coding contests for Web3 developers to showcase their skills while working on different projects to earn rewards. These contests enable developers to identify bugs and vulnerabilities in smart contracts, while also enhancing their coding skills.
-
Sherlock.xyz — Sherlock offers a crowdsourced security challenge that provides a gamified experience for security researchers, hackers, and developers to test their skills and earn rewards. Sherlock challenges consist of several stages, with each stage containing hidden vulnerabilities and puzzles to solve. Participants are rewarded with bounties for discovering vulnerabilities and submitting proof of concepts.
-
Hackenproof — Hackenproof is a blockchain security firm that provides a platform for reporting security vulnerabilities. Hackenproof offers clients access to a huge network of highly experienced security researchers who can identify security flaws in web applications and blockchain-based systems. The platform is built around transparency, and rewards are paid out consistently and transparently.
Audits Distilled
Looking at this month’s never-ending hacks, one may wonder why they happen so frequently…
Have audit firms actually gotten worse at what they do???
This might not be the case, however, it’s obvious that the quality of the auditing services differs dramatically from company to company, so it’s vital for the project to choose the right vendor with an untarnished reputation trusted by the leaders to run its code vulnerability check.
Formal verification of smart contracts works by presenting the logic and desired behavior of smart contracts as mathematical statements. Auditors then use automated tools to check if these statements are correct. Usually, formal verification is a part of audit.
Typically, audits conclude with clients receiving a report containing auditors’ observations about the security of the system. In many cases, an audit report will highlight security issues discovered while inspecting the project’s codebase and will make recommendations for resolving such issues before releasing an application to the public.
https://officercia.mirror.xyz/FvMKbibx7gDlufgZSkmYn77CI8HPBsVCeqUKmpXHr0k
While manual inspection of contract code by expert auditors is advantageous, it can be difficult to scale, causing projects to face lengthy delays before deploying to mainnet.
However, more audit firms are using their expertise to create proprietary and open-source software for automatic vulnerability detection. Development teams can use such tools to help with testing and free up auditors’ time to focus on errors missed during automated testing.
I highly recommend that you read the following study, which in my opinion is the most revealing of aspects of the changes in the sphere in 2022–23:
https://consensys.net/diligence/blog/2023/05/charting-the-web3-security-landscape/
Certain layers of the web3 security stack remain underutilized, which will most likely change as the industry matures. DeFi projects, in particular, may begin to broaden the scope of security activities to include proactive threat monitoring and response, as well as automated risk management (rather than focusing solely on vulnerability assessments).
Logically, cybersecurity must be considered on every level of project development — with contests on the guard at the initial stage, followed by audits, and then bug bounties — at the final stage. No doubt, a new generation of cybersecurity products are already on the way that will cover all these aspects in one user-friendly interface.
https://blog.pessimistic.io/spotters-almanac-4c594fd834d1
Advantages & Disadvantages
This has drawbacks of its own; for instance, novice hunters may conduct attacks on the mainnet or even publicly disclose the vulnerability, which may have an impact on the token’s value, the capitalization, or the stock price. One may even state that existing solutions like manual audits, static analysis, and fuzz testing lack mathematical soundness and scalability…
https://github.com/blockthreat/blocksec-ctfs
The interest of major players is also present where there are opportunities for such manipulations…
That said, advantages of web3 bug-bounty programs include:
-
Increased Security: By encouraging developers and security researchers to identify and report vulnerabilities in web3 applications and protocols, bug-bounty programs help to enhance security and protect against potential hacks.
-
Risk Mitigation: By identifying vulnerabilities early on, bug-bounty programs can help to mitigate the risks associated with any potential attack.
-
Cost Savings: Detecting vulnerabilities early can save an organization significant amounts in potential losses from a cyber-attack.
However, there are also some disadvantages to web3 bug-bounty programs, which include:
-
False Positives: Not all reported vulnerabilities will be legitimate, leading to wasted time and effort for both the organization running the program and the developers reporting the issues.
-
Limited Scope: Bug-bounty programs have a limited scope, and vulnerabilities that exist outside of the scope of the program may go undetected.
-
Incentive Misalignment: There may be instances where developers report vulnerabilities to multiple bug-bounty programs, which can create a misalignment of incentives.
But what if the project refuses to pay?
Surprisingly, but in the classic platforms it is real, in part, so — to raise confidence in the eyes of bug-bounty hunters and were created new sites where the payment is provided initially that creates a sense of trust.
However, this can be dealt with, for example, by publicity:
https://bug-bounty-wall-of-shame.github.io/
That said, Web3 bug-bounty programs also can be (and they actually are) an effective way to incentivize the identification and reporting of vulnerabilities in blockchain protocols and decentralised applications.
There is also such an awesome thing as a skin-in-the-game auditing mechanism. So, the centralized auditing firms in the skin-in-the-game auditing accept to deposit a portion (30–60%) of their service fee to the projects bug bounty for a period of time (3–12 months) to share the risk after their audit.
However, they are not without their limitations, and organizations should be aware of these limitations when implementing bug-bounty programs…
As you probably already know, the whole DeFi industry was very painfully hit by the recent hack of the Euler protocol. The incident left the protocol devastated and led to a chain of damage to the entire Lego-based DeFi ecosystem…
Despite the fact that only one of the sherlock.xyz contest covered the vulnerable code in one way or another, the event cast a shadow over the auditing business and the entire industry and forced the public to raise important questions…
All this leads us to the idea that in the end it will be important for the project to have multiple levels of protection — several audits from different companies and several bug-bounty programs on platforms with different features.
New Generation of the Web3 Security
New bug-bounty platforms try to solve several problems that previous versions obviously lack. For instance, they more actively interact with the community, and often their structure is built so that people are allowed to participate even without KYC (as in more classic sites where such conditions are determined by the end customer represented by the project or protocol). Very often they also implement the Zerodium model and collect data.
http://twitter.com/maurelian_/status/1669045637235572737
However, they are still short on functionality and possess numerous shortcomings that should be addressed.
https://cointelegraph.com/magazine/defi-security-audits-bug-bounties-broken-heres-how-fix/
The next generation of Web3 security platforms will go beyond current limited solutions, applying advanced tools and technologies and providing superior usability to all industry players.
To let us know your interests and preferences better, please fill in a short questionnaire!
https://docs.google.com/forms/d/e/1FAIpQLSckhaBICyiJLanepidb6MEcuoMX7826bmMDcJaIm21Yf0LEuQ/viewform
My good friends are about to launch their project, which in my opinion will be the ultimate game changer for the whole industry. They seek to reshape every aspect of the project’s cybersecurity lifecycle and become a one-stop point for assets and data protection. If you are interested, please follow their Twitter & Discord and stay tuned for the updates!
Join the Discord server below:
Thank you!
By the way, there are some vacant slots now so if your project needs an audit — feel free to write to us, visit our public reports page here!
Support is very important to me, with it I can do what I love — educating users!
https://github.com/OffcierCia/support
If you want to support my work, you can send me a donation to the address:
-
0xB25C5E8fA1E53eEb9bE3421C59F6A66B786ED77A or officercia.eth — ETH, BSC, Polygon, Optimism, Zk, Fantom, etc
-
4AhpUrDtfVSWZMJcRMJkZoPwDSdVG6puYBE3ajQABQo6T533cVvx5vJRc5fX7sktJe67mXu1CcDmr7orn1CrGrqsT3ptfds — Monero XMR